SSL disappears from the certificate list on Windows server
Thank to: https://www.namecheap.com/
Users with Windows servers may occasionally encounter an issue when an imported certificate disappears from the list of server certificates. Most often, this happens right after completing certificate request in Internet Information Services (IIS) Manager or Exchange Management Console and refreshing the list of certificates.
The lists of server certificates in IIS and EMC contain only certificates that are assigned to the corresponding private key and generated along with the certificate signing request (CSR) used for activating a particular certificate. When the link between certificate and private key is broken for some reason, the certificate disappears.
In order to make the certificate reappear, you will need to force the link between the certificate and the private key using the following steps:
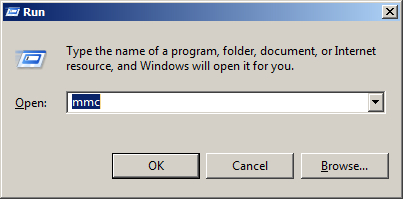
- Open Microsoft Management Console (MMC) on your server machine. Make sure that you are logged as administrator before proceeding. To open MMC, press Win+R combination, type in mmc and click OK.
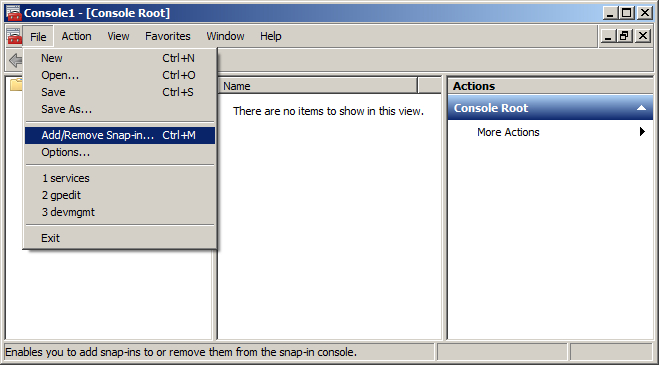
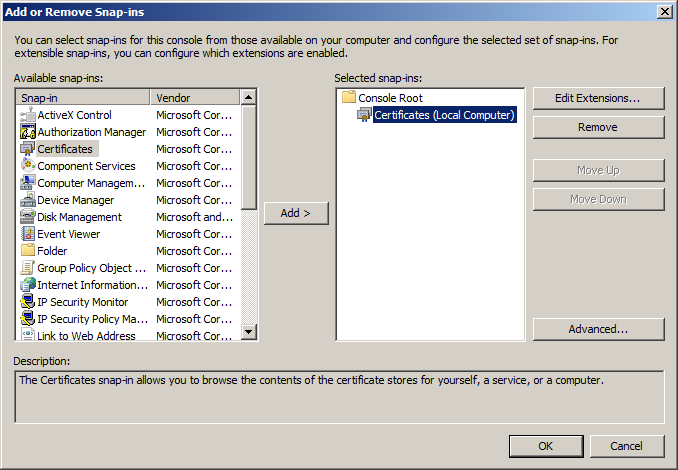
- In File menu, select Add/Remove Snap-in.
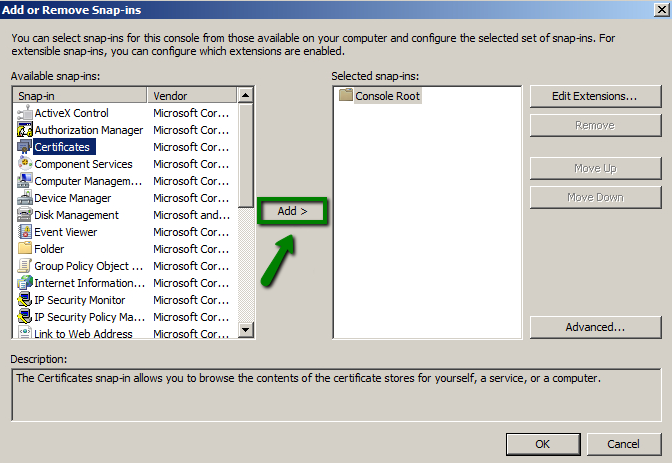
- In the Add or Remove Snap-ins dialogue window, select Certificates and click Add.
- Choose Computer account in the Certificates snap-in window, click Next.
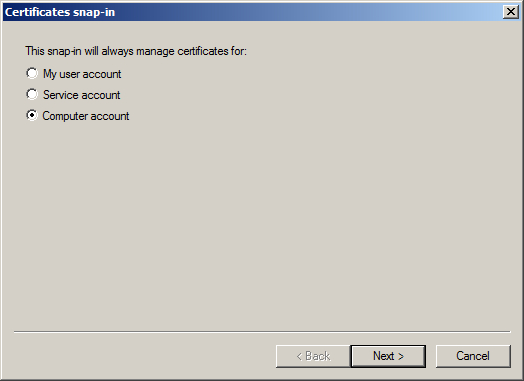
- Tick Local computer in the Select computer box, then click Finish.
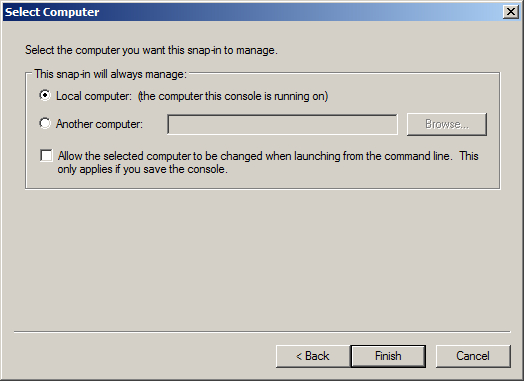
- The required snap-in is selected now. Click the OK button to proceed. The snap-in is now added to console.
- Locate the certificate that was imported when completing certificate request. The certificate should be in Personal store. Note that the icon of the certificate next to the domain name does not have a key on it; that means that no private key is assigned to the certificate.
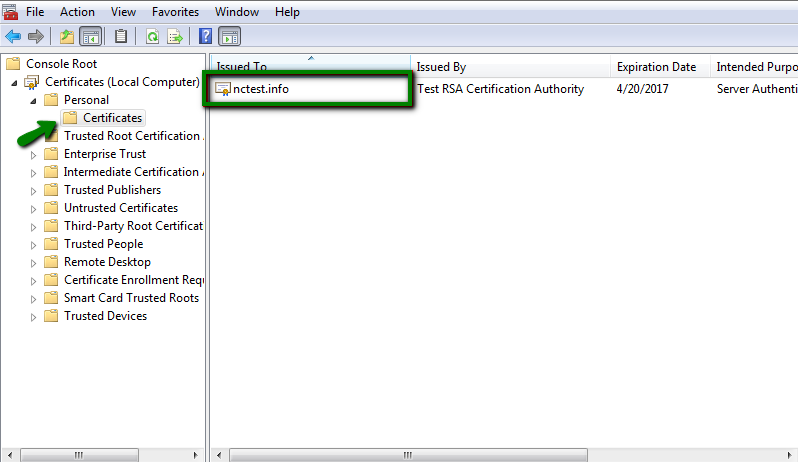
- Double-click the certificate and go to Details tab.
- In certificate details locate the Serial Number field, click on it and copy its value.
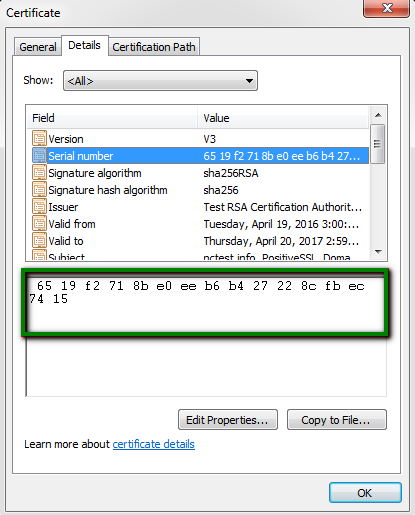
- Open Command Prompt, pressing Win+R and typing cmd, then click OK
- In the command prompt type: certutil -repairstore my Serial_number from step 9Note: Make sure the serial number of your certificate does not contain any spaces. It should be a single string of symbols.
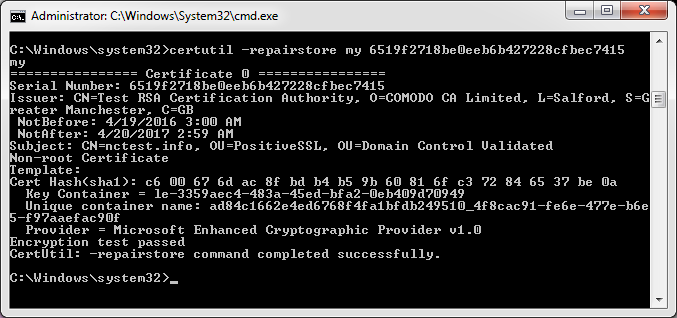 If you receive “CertUtil: -repairstore command FAILED: 0x80090010” error, this means that the certificate request was generated on another server, and the private key is absent on this one. You need to either transfer the key to your server via PFX file or create a new CSR code and reissue the certificate.
If you receive “CertUtil: -repairstore command FAILED: 0x80090010” error, this means that the certificate request was generated on another server, and the private key is absent on this one. You need to either transfer the key to your server via PFX file or create a new CSR code and reissue the certificate. - Refresh the list of certificates in Personal certificate store in your MMC. The certificate icon should have the key on it.
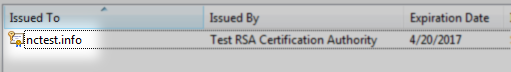
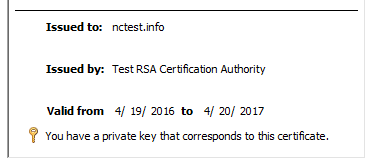
Additionally, if you double-click the certificate, you will see the message: “You have a private key that corresponds to this certificate.”

You can now refresh the list of server certificates in IIS Manager or Exchange Management Console to see the certificate there.
The same instructions may be used if the certificate was deleted from the server. If you delete a certificate, the corresponding private key remains on the server. This means that the certificate can be imported back to the server via MMC (you can download the certificate in your account, provided it was purchased with Namecheap, and take the steps from this article to import the certificate to your machine. The only difference is that the certificate should be imported into Personal store) and certutil command used to restore the link between the private key and the certificate.


Comentarios
Publicar un comentario
Dime si la información de este blog te sirvio.