IPsec VPN between static and dynamic IP (FQDN) in Fortigate
- Obtener enlace
- X
- Correo electrónico
- Otras aplicaciones
Thanks to: https://community.fortinet.com/
Solution
One of the local FortiGate the dynamic IP address is used (in this case, a remote firewall FQDN address) as a remote-gateway.
Phase I and Phase II configuration.
1) Configuration of phase 1, where we are using the type as DDNS.
# config vpn ipsec phase1-interface2) Configuration of phase2.
edit "frtest"
set type ddns <-----
set interface "wan1"
set peertype any
set net-device disable
set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1
set wizard-type static-fortigate
set remotegw-ddns "testbran.fortiddns.com" >>>>FQDN address
next
# conf vpn ipsec phase2-interfaceNote.
edit "frtest"
set phase1name "frtest"
set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256 aes128gcm aes256gcm chacha20poly1305
set src-addr-type name
set dst-addr-type name
set src-name "frtest_local"
set dst-name "frtest_remote"
next
end
The remote-end firewall has a dynamic IP address instead of a static IP address, so an FQDN (fully qualified domain name) in the gateway configuration.
Below configuration on remote FortiGate in GUI.
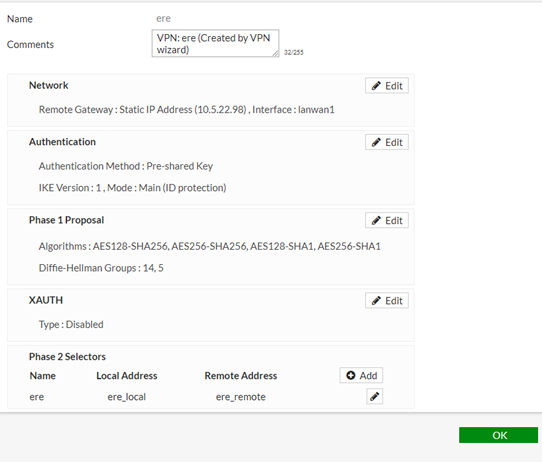
Go to VPN -> IPsec Wizard .
- Set the Name <ere>
- Select the Template type Site-to-Site
- Set the Remote IP address <static IP address>
- Select the local interface and subnets.
After the above setup, the similar as shown below is visible (the Remote Gateway is Static IP address which is 10.5.22.98 in this example).
FGT # diagnose vpn ike gateway list
vd: root/0
name: frtest
version: 1
interface: wan1 7
addr: 10.5.22.98:4500 -> 10.5.21.219:64916 <----- Resolved FQDN IP is listed.
created: 3199s ago
nat: peer
IKE SA: created 1/2 established 1/1 time 20/20/20 ms
IPsec SA: created 1/2 established 1/1 time 20/20/20 ms
id/spi: 23274 fdc5a41724a8e065/ed8c3e19adb75840
direction: responder
status: established 3194-3194s ago = 20ms
proposal: aes128-sha256
key: 3c359876a94b04d2-b70eade19fc29822
lifetime/rekey: 86400/82935
DPD sent/recv: 00000000/00000000
Configure dial-up (dynamic) VPN
Dial-up, or dynamic, VPNs are used to facilitate zero touch provisioning of new spokes to establish VPN connections to the hub FortiGate.
The exchange-interface-ip option is enabled to allow the exchange of IPsec interface IP addresses. This allows a point to multipoint connection to the hub FortiGate.
The add-route option is disabled to allow multiple dial-up tunnels to be established to the same host that is advertising the same network. This dynamic network discovery is facilitated by the BGP configuration;
Wildcard security associations are defined for the phase2 interface because routing is used to determine if traffic is subject to encryption and transmission through the IPsec VPN tunnel. The phase1 interface name must be 11 characters or less.
A dynamic VPN configuration must be defined for each interface that connects to the internet.
To configure the IPsec phase1 interfaces:
config vpn ipsec phase1-interface
edit "vpn-isp-a"
set type dynamic
set interface "port2"
set peertype any
set exchange-interface-ip enable
set proposal aes256-sha256
set add-route disable
set dhgrp 5
set net-device enable
set psksecret ********
next
edit "vpn-isp-b"
set type dynamic
set interface "port3"
set peertype any
set exchange-interface-ip enable
set proposal aes256-sha256
set add-route disable
set dhgrp 5
set net-device enable
set psksecret ********
next
endTo configure the IPsec phase2 interfaces:
config vpn ipsec phase2-interface
edit "vpn-isp-a_p2"
set phase1name "vpn-isp-a"
set proposal aes256-sha256
set pfs disable
set replay disable
next
edit "vpn-isp-b_p2"
set phase1name "vpn-isp-b"
set proposal aes256-sha256
set pfs disable
set replay disable
next
end- Obtener enlace
- X
- Correo electrónico
- Otras aplicaciones

Comentarios
Publicar un comentario
Dime si la información de este blog te sirvio.